In today’s dynamic digital world, security has become a priority for both organizations and individuals. Security systems are evolving, and data protection technologies are continuously advancing. However, despite these efforts, unnoticed areas remain — gaps in security systems that cybercriminals can exploit to conduct attacks and steal valuable information while remaining undetected.
There is only one thing worse than an intruder in your network: an unnoticed intruder in your network. Blind spots (areas outside the visible range) can turn a momentary incident into a months-long cybercriminal operation within an organization, leading to significant data loss and difficult to eradicate infections. Attackers are keen to exploit any opportunity to leave behind numerous backdoors. Case studies reveal that security blind spots often enable financially motivated APT (Advanced Persistent Threat) groups to deploy ransomware solutions within targeted environments. Once inside a network, attackers bide their time, waiting for the right moment to stealthily access critical internal resources and ensure that ransomware’s reach is as wide as possible, including sabotaging recovery mechanisms.
What Are Security Blind Spots?
Blind spots are weaknesses in security strategies and implementations that remain unnoticed or insufficiently protected. These vulnerabilities can stem from several factors:
- Human negligence: Mistakes made by employees, such as using weak passwords, clicking on suspicious links, or carelessly sharing sensitive data.
- Lack of threat awareness: Insufficient knowledge of the latest attack methods and security vulnerabilities can lead to a failure to recognize potential threats.
- Outdated systems and software: Older software versions often contain known vulnerabilities that hackers can exploit.
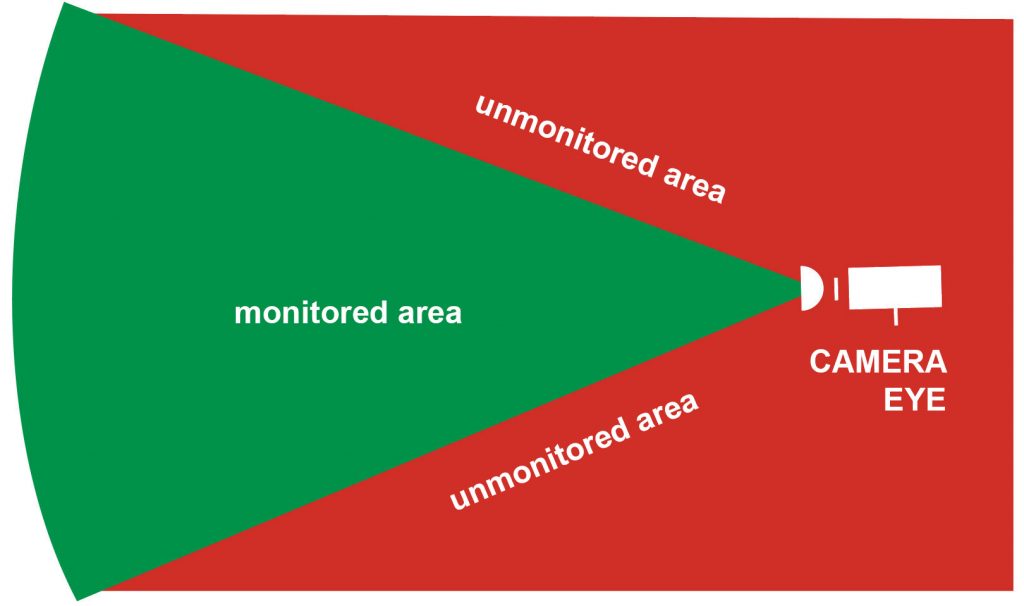
To visualize security blind spots, consider them analogous to unseen areas in CCTV monitoring of physical locations. While monitoring provides some level of situational awareness, many gaps remain, allowing intruders to operate unnoticed.
Types of Blind Spots in Cybersecurity
- Technological gaps:
- Vulnerable software: Outdated operating systems, applications, and network software can harbor known weaknesses.
- Unsecured IoT devices: IoT (Internet of Things) devices, such as IP cameras, smart speakers, and thermostats, often lack strong security measures, serving as gateways into internal networks.
- Human errors:
- Phishing: Phishing attacks involve impersonating trusted entities to steal sensitive data, such as login credentials.
- Social engineering: Psychological manipulation by attackers can persuade employees to divulge confidential information or perform actions harmful to the organization.
- Organizational oversights:
- Lack of a clear security policy: The absence of defined procedures and rules for data protection can lead to unintentional data leaks.
- Lack of monitoring mechanisms: Actions by employees and third parties may go unnoticed, including Shadow IT activities or subcontractor operations.
- Infrastructure weaknesses:
- Unsecured Wi-Fi networks: Poorly protected wireless networks can enable attackers to access transmitted data.
- Lack of physical access controls: Unmonitored access to server rooms and other critical infrastructure can result in equipment or data theft.
How to Identify Blind Spots?
Identifying blind spots is a critical component of an effective security strategy. The following methods can help:
- Security audits: Regular audits conducted by independent experts can help identify gaps in security systems.
- Penetration testing: Simulated attacks by security specialists assess the effectiveness of existing measures and reveal potential vulnerabilities.
- Log analysis: Monitoring system logs can help detect suspicious activities and anomalies that may indicate an attack.
- Employee training: Ongoing cybersecurity training enhances employee awareness of threats and teaches them to recognize and avoid potential traps.
How to Eliminate Blind Spots?
The nature of blind spots lies in the lack of awareness, either situational or technical, among those who manage infrastructure security. Addressing blind spots entirely is a significant challenge requiring not only direct action but also the implementation of effective prevention procedures. The focus should be on risk minimization.
Mitigating risks from blind spots requires a comprehensive approach, including:
- Implementing multi-layered protection: Utilizing multiple security mechanisms, such as firewalls, antivirus software, and intrusion detection systems.
- Updating software: Regular updates of operating systems, applications, and network software to eliminate known vulnerabilities.
- Security Gap Analysis audits: Comparing the expected state of security with the actual state to uncover hidden vulnerabilities and provide recommendations for addressing them.
- Employee training: Cybersecurity education is crucial for preventing socially engineered attacks.
- Regular security audits: Ongoing evaluations ensure new vulnerabilities are identified and addressed.
Conclusion
Blind spots in security pose a significant threat to both organizations and individuals. Identifying and eliminating these vulnerabilities is essential to ensure the effective protection of data and IT systems. A comprehensive security approach that addresses technological, human, and organizational aspects, following a Defense-in-Depth strategy, is critical in an ever-changing digital landscape.
It is imperative to emphasize, that security is a continuous process requiring constant attention and adaptation to evolving threats. This process must be nurtured at every step, from work organization and competency verification to direct management of business and security systems.