Hi! How did you spend your last day? Did you listen to music online? Perhaps you watched some movies or series? Many people had order food delivery through apps. Others did online shopping, paid via the Internet, and are waiting for the delivery. The daily routine of each of us depends to a large extent on the Internet. How many tasks of your last day were also dependent on access to the network? How much time would it cost you if you didn’t have such access? How many nerves? Fortunately, such problems are less and less common. Millions of engineers work every day, contributing to the global network infrastructure that creates the Internet that we all know very well. Today I will tell you shortly about how the Internet works, so you can understand what DDoS attacks are, how they work, and how TAMA provides comprehensive protection to ensure uninterrupted global network access for users.
As you probably know, from the perspective of an average user, the Internet is a network access service, provided by an ISP (Internet Service Provider). In a nutshell the Internet allows for “conversation” (exchange of information) between the devices located in different places around the world. Whether we’re watching a movie, ordering food, or searching for information we always connect to a device (computer) that someone has prepared for us. To be able to do that, ISP need to know who is communicating with whom and where both sides of this exchange are located. In practice, this is achieved using a set of interconnected network devices, which, like the devices being serviced, must be geographically dispersed. In every ISP network, we can find various (sometimes bizzarre) devices, but today we will focus on routers – devices specifically responsible for delivering data to the right place.
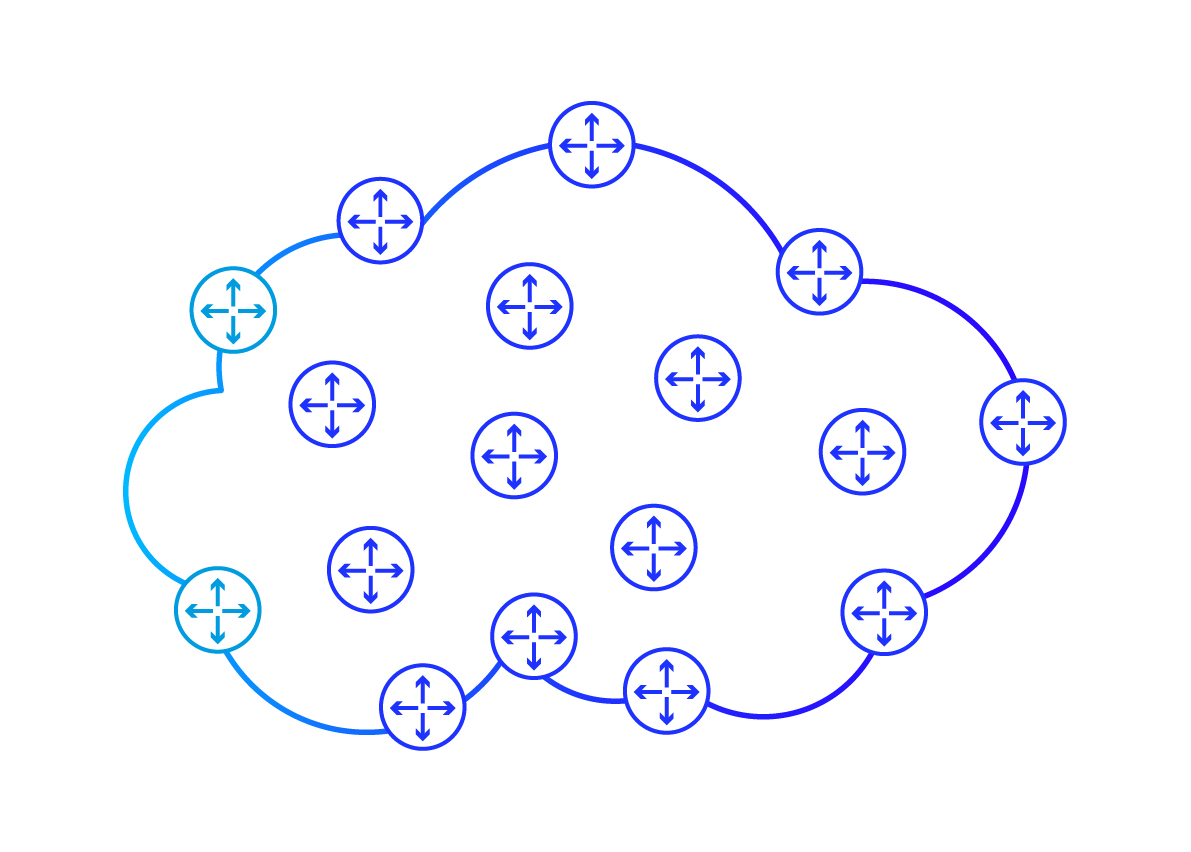
The above diagram picture an example layout of routers in an ISP network. The cloud visible in the background depicts the network boundaries. The dispersion of routers in the diagram corresponds to their geographical distribution – each of them is located in a different place. Particularly noteworthy are the routers located directly at the edges of the network.
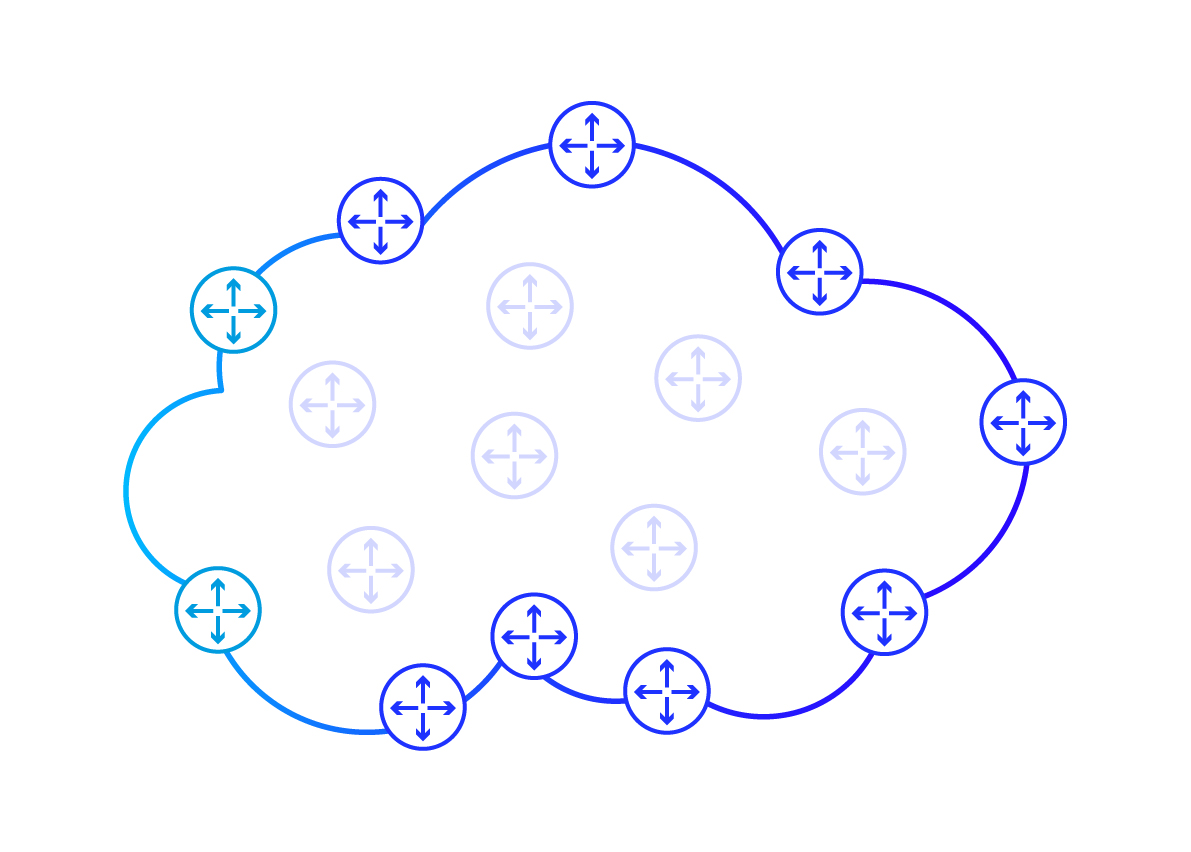
These are called edge routers (PE Router; Provisioner Edge Router). They are particularly important to us because they are the only points through which data can enter or exit the ISP network . Connected to these routers are all kind of user devices (such as probably the one you are using to read this article) and servers (including the one from which you read this article).
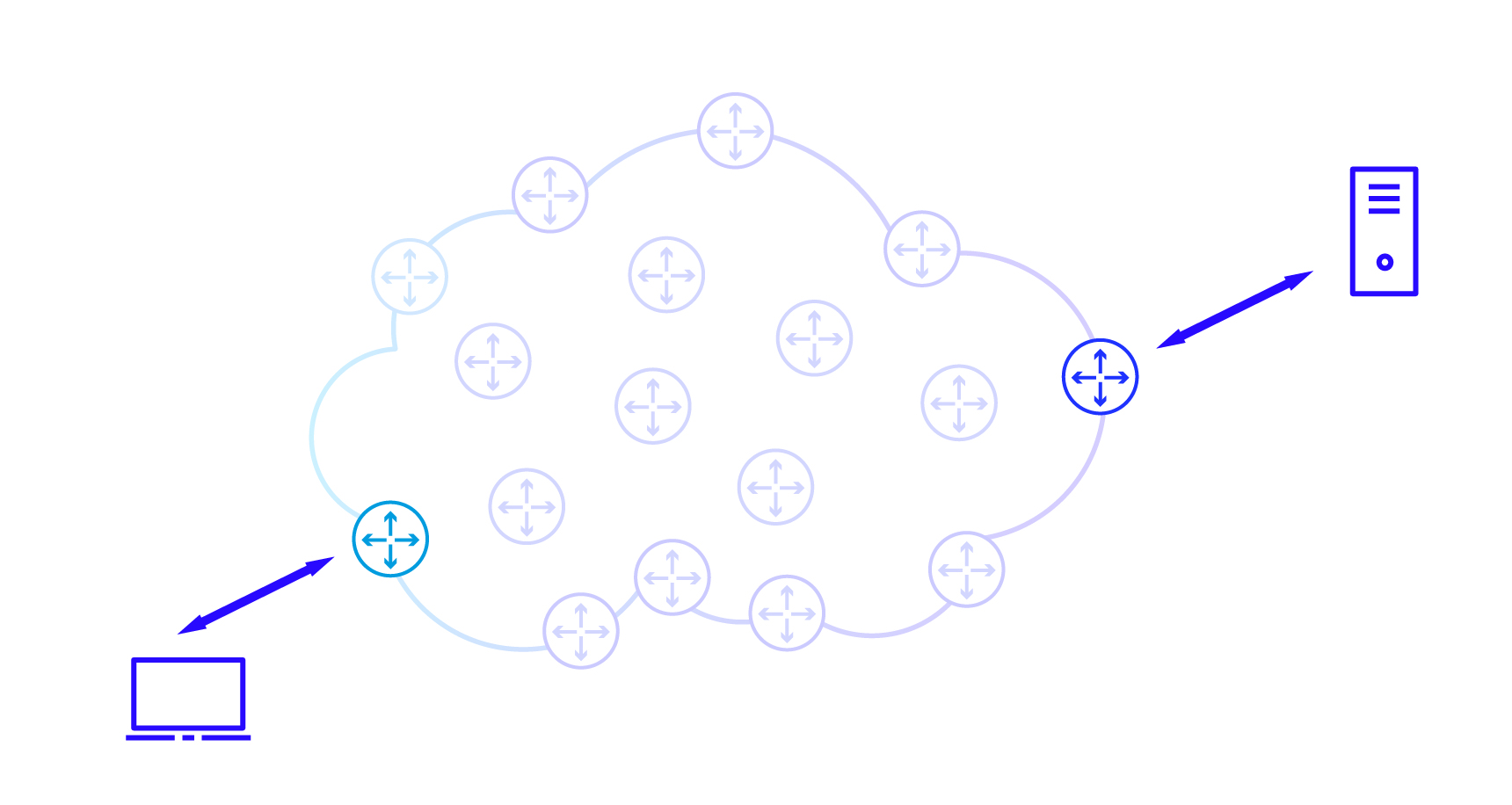
A lion’s share of communication on the Internet occurs between pairs of specific devices. To enable routers to locate them in the network, each is assigned a special number – an IP address (for practical reasons, they are represented as 4 numbers, hence instead of 134 744 072, we see 8.8.8.8). In my youth, this term was often misused. Have you ever heard someone saying they will “hack your IP”? Truth be told, the IP address is a crucial element of communication. When initiating a connection (starting a “conversation”) on the Internet, the initiator needs to know who the message is addressed to (know the recipient’s IP address). For the message to reach its destination at all, the ISP must relay it to the right place (hence the IP address must be visible to them), at the same time, the recipient should be able to respond to such a message (hence the sender must provide their own address). As a consequence the IP address is visible to both the participants as well as an ISP.
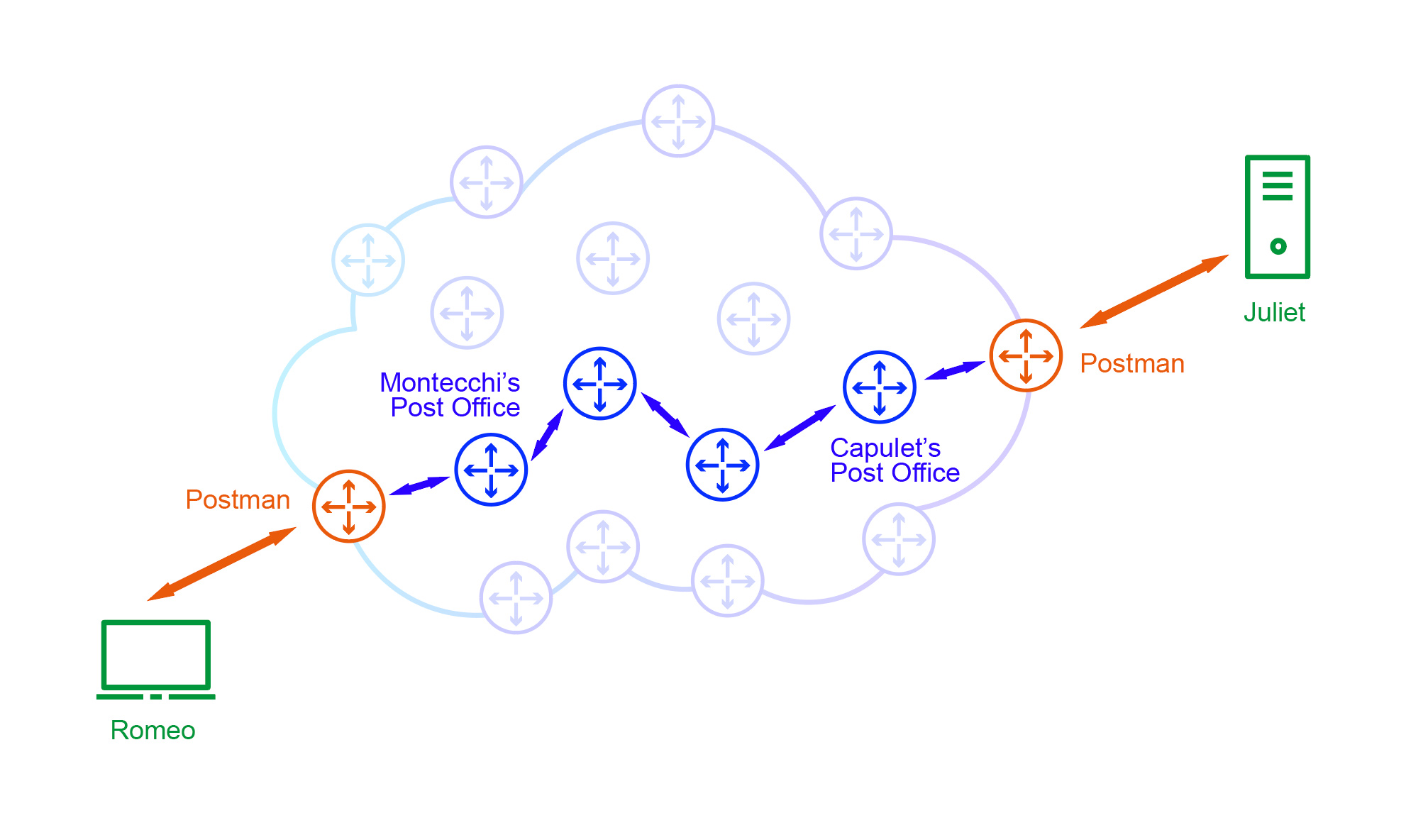
You’ve probably also heard that the IP address is like a home address. Thinking about it this way, communicating devices exchange letters, and the ISP serves as a post office. The home address is visible on the envelope to all involved in the exchange of information. Following this metaphor, the post office does not deliver the letter directly from point A to point B (as it would be impractical). Instead, the postman picks up the letter, post offices sort the mail based on the destination address, and pass it on to the next offices until finally, the local postman delivers it to the recipient. The aforementioned routers serve as such post offices here. Both routers and post offices are not interested in the entirety of communication or even where a given letter came from. They have only one task: sort the mail based on the destination address and pass it on to the next neighboring post office/router – always towards the addressee. Edge routers act as local mail carriers here, exchanging mail between post offices and recipients.
It is said that genius lies in simplicity, and as it turns out, the Internet (and mail) is built on incredibly simple mechanics. If we step outside the framework of a single conversation and look at the scale of the entire process, we can quickly be overwhelmed by its effectiveness.
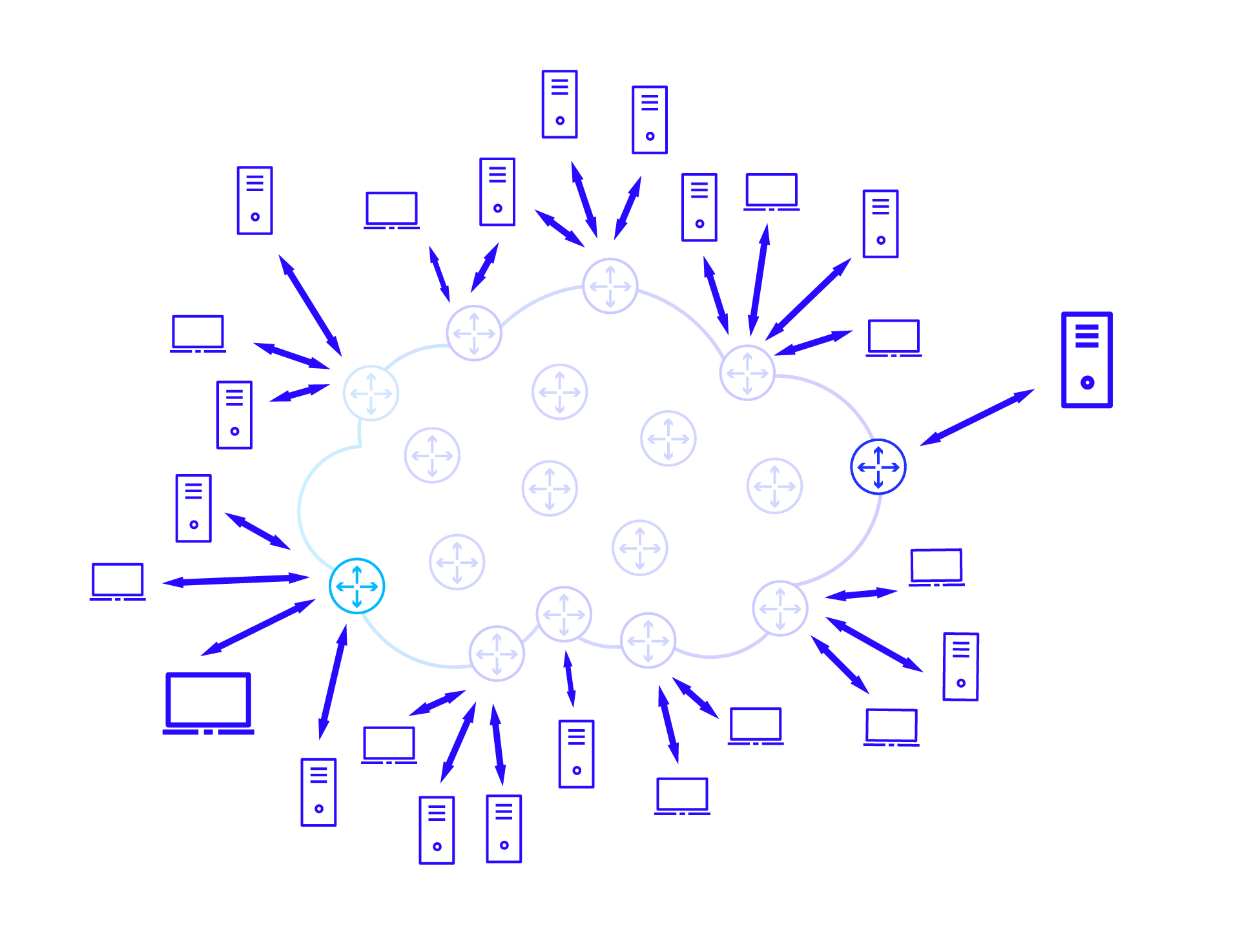
Millions of different devices are connected to large ISP networks, between which information is exchanged continuously (there are only 26 of them pictured on the diagram above). The whole system operates so effectively mainly because each router (just like each post office) works independently and handles only the data in its area of operation. This can be illustrated by depicting communication routes between various pairs of devices.
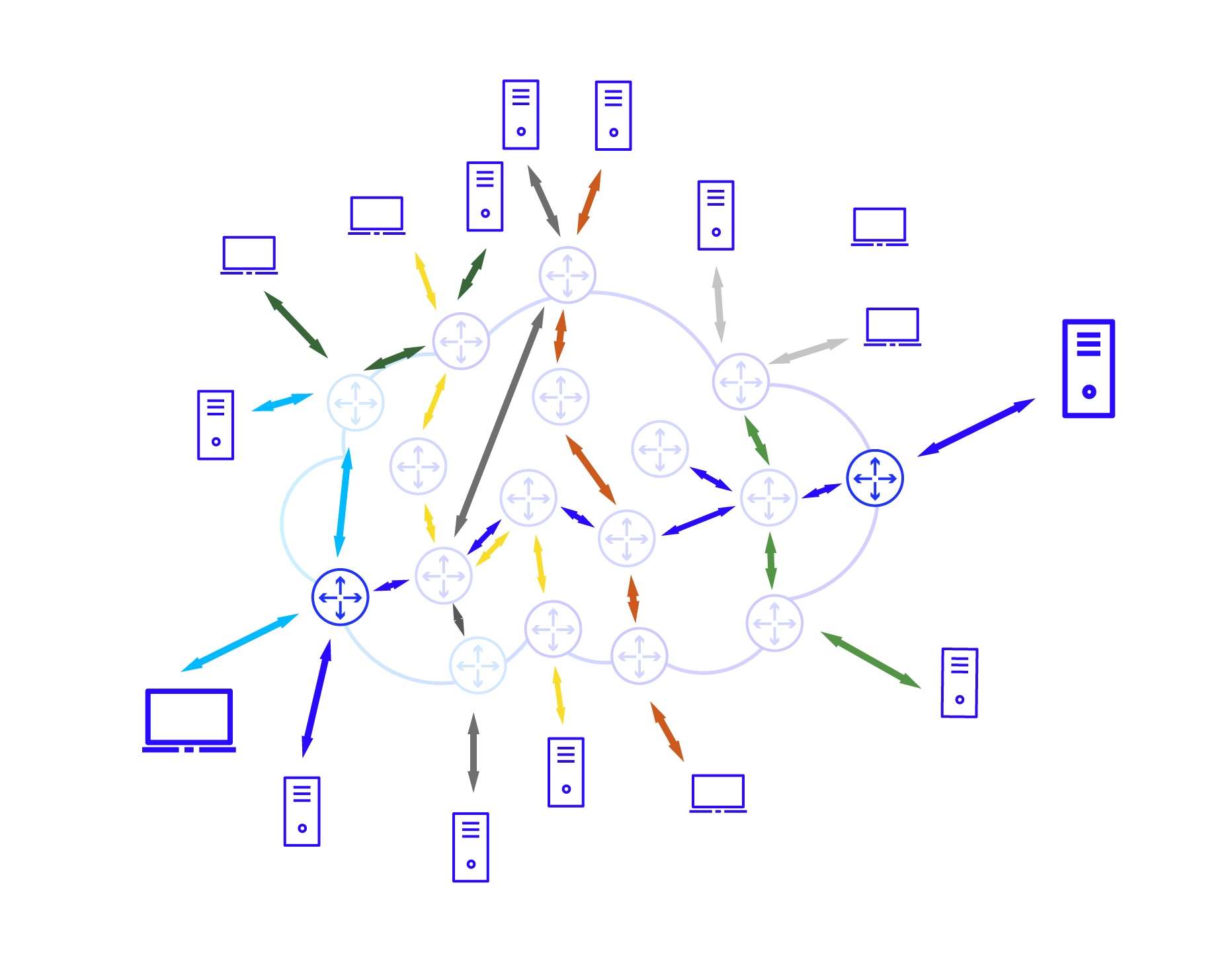
The diagram above clearly shows that the load in one area of the network does not affect the others (each router handles its own packets), which, combined with the fairly chaotic nature of Internet traffic (meaning data is exchanged in all directions), allows for a relatively balanced load across the network, thus guaranteeing access to the Internet for a tremendous number of users.
Somewhere in there lies “him” – the bad guy!
Let’s return for a moment to the diagram depicting how the Internet works in the metaphor of mail.

If you are familiar with Shakespeare’s drama, you probably know that the Montague and Capulet families wasn’t really fond of each other, and the only exception were the main characters, Romeo and Juliet. We can confidently assume that both families tried to limit contact between the main characters. However, they couldn’t do anything about their epistolary relationship, transmitted through private & confidential mail that can be only received in person. Fulgencio Capulet (Juliet’s father) had very good understanding of how mail worked, which allowed him to devise a clever scheme that effectively prevented the lovers from communicating. He sent thousands of letters to his friends and subjects throughout the Italy. Each of them reads the same: “Send as many letters as possible to my daughter Juliet. The content doesn’t matter as long as they are addressed to Her.”
Following Lord Capulet’s instructions, thousands of people began writing tens of thousands of letters, each addressed to one person. Post offices across the country suddenly started directing more and more letters to one clearly defined place.
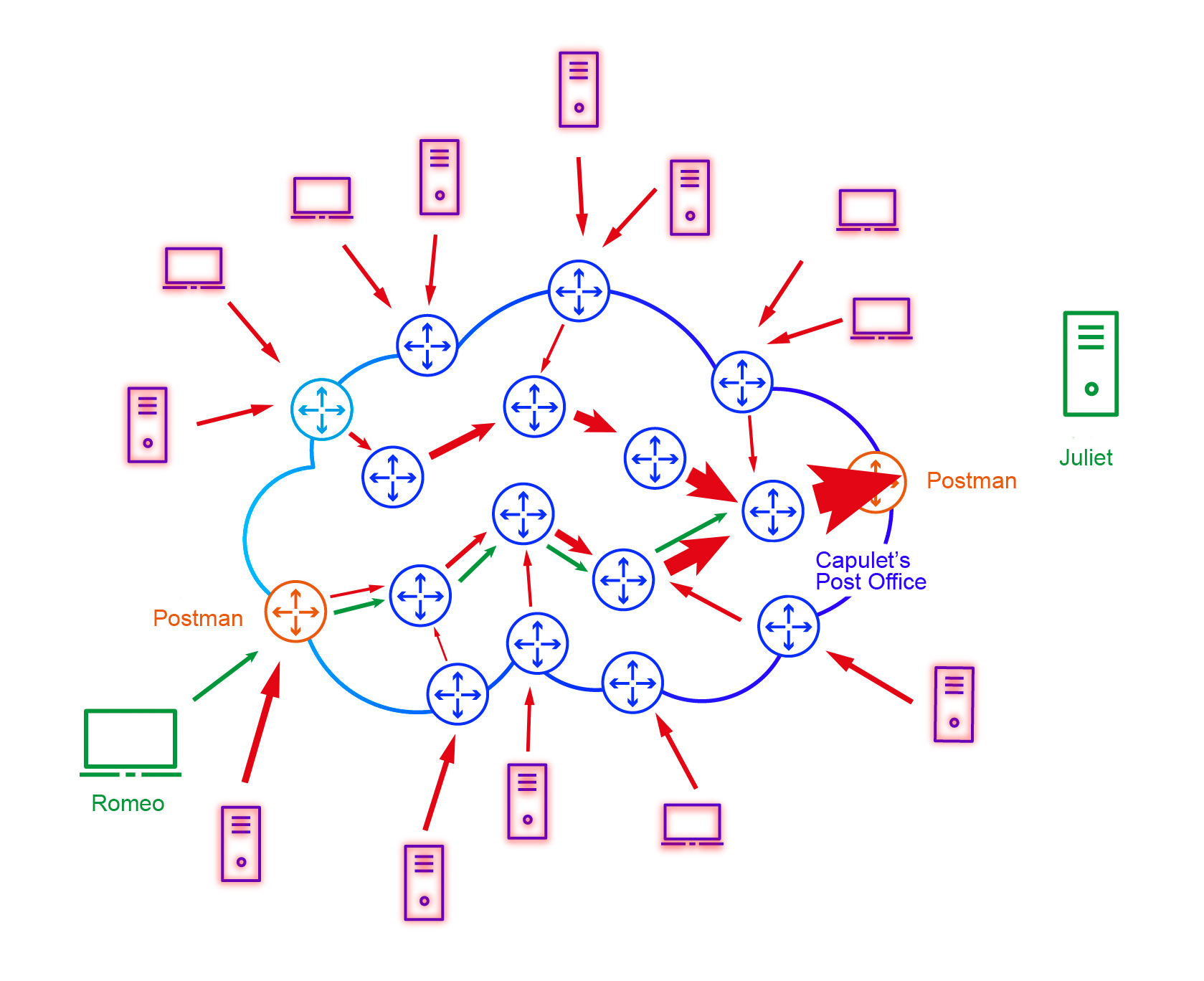
The diagram above illustrates the effects of the Capulet’s head scheme. The red arrows represent unwanted correspondence directed to his daughter, while their thickness represents the number of letters. As expected by the cunning lord, the Capulet mail was flooded with an enormous number of letters, arriving faster than the employees could sort them. This, in turn, froze the operation of the post office, preventing any letters from leaving the facility. As a result, although our main characters continued to send letters to each other, none of them reached the recipient. At the same time, all other post offices operated normally because none of them were inundated with such a volume of work as the Capulet mail.
The story illustrates how the simplest DDoS attacks work. Why was such an attack effective? What could the post office do to prevent such an attack? What could Romeo and Juliet do? How could the feuding houses respond? And what it has to do with ordering a kebab delivery? We’ll address all these questions in the next part of the article.
***
[1] In reality, routers can be very close to each other but are responsible for handling different geographical areas. Increasingly, you can encounter situations where the location of routers is completely detached from the physical location of the connected devices for more effective network management and faster communication between devices.
[2] For the purposes of this article, I have made a simplification, but there are situations where this is not true. Many Internet services rely on intermediaries. Often, when playing an online game, we do not communicate directly with other players, but only with the server hosting the game. In such cases, each player knows the server’s address, the server knows the address of each player, but the players do not know each other’s addresses. In such a case, players cannot communicate over the Internet directly because they do not know each other’s addresses. Proxy services operate on similar principles. Referring to the mail metaphor, we can say that one of the post offices repackages the message into another envelope so that the other side does not learn our address.
Read also:
>>> Mission: TAMA to be forced through. Day one: recognition






